Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. Reporting the attack to law enforcement and other authorities. Your feedback is private. There is no NIST cybersecurity certification. If the integrity of data was affected or content deleted, have a plan in place for restoring it. For most companies, the first port of call when it comes to designing a cybersecurity strategy is the National Institute of Standards and Technology (NIST) Cybersecurity Framework. Network Computing is part of the Informa Tech Division of Informa PLC. In fact, around 7 out of every 10 security professionals and IT experts agree that the NIST framework is a good idea and that implementing it is a best practice. There is, however, a NIST cybersecurity implementation certification. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. The result is better communication and decision-making throughout your organization. There is no reason not to. Though were unable to respond directly, your feedback helps us improve this experience for everyone. Private Equity firms pride themselves on implementing best practices in every functional area within their portfolio companies. I did offer comments as an individual, but also, in my past employers, to the particular products. For more of our videos, please be sure to visit SearchSecurity.com/videos. The NIST Cybersecurity Framework specifies four implementation tiers. You can use the built-in firewall of your router, or install a separate firewall device or software on your network. The non-regulatory agency accomplishes this goal by developing technology, metrics, and standards. Ernie is an Executive Consultant with Securicon. The NIST Cybersecurity Framework seeks to address the lack of standards when it comes to security. There are a number of pitfalls of the NIST framework that contribute to. The higher the tier, the more compliant you are. Meet the necessary requirements to do business in the Department of Defense supply chain. Again, this matters because companies who want to take cybersecurity seriously but who lack the in-house resources to develop their own systems are faced with contradictory advice. What we need is guidance, we need to give people a sense of the "how-to's," "How do I achieve that particular result?" According to cloud computing expert Barbara Ericson of Cloud Defense, Security is often the number one reason why big businesses will look to private cloud computing instead of public cloud computing.. Preparation includes knowing how you will respond once an incident occurs. You can also use tools like Aircrack-ng, Kismet, or Wifite to test your network security and see if it can withstand common attacks like cracking, spoofing, or denial-of-service. What else would you like to add? Have formal policies for safely disposing of electronic files and old devices.
!3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf Companies are charged a fee to access the ISO 27001 documentation. Using a gold standard like the CSF fosters trust between your partners and enables faster business growth while staying secure. The problem is that many (if not most) companies today. Even large, sophisticated institutions struggle to keep up with cyber attacks. These are the tasks or challenges associated with each category. The implementation process may seem cumbersome, but you can be more secure. Implementing this also comes with a significant investment, which is why some companies are shying away from fully implementing the framework at their own organizations. Keep employees and customers informed of your response and recovery activities. Looking for legal documents or records? Web00:00. 2) Identifying new standards and policies to improve cybersecurity measures. For example, NIST had mentioned that they would like to work around encryption. Search the Legal Library instead. Tags: Learn more about our mission, vision, and leadership. Present actionable insights in terms that clearly illustrate cybersecurity posture. <>
CIS Controls: a concise, prioritized set of cyber practices created %
The second issue was to be performance based, was really critical, because a lot of us were very concerned that the NIST product was going to be a compliance driven product, fortunately, it wasn't. The Trump administration has decreed that each agency should have their own implementation plan ninety days after the executive order was signed in May 2017. Informative sources. 6 0 obj
We are right next to the places the locals hang, but, here, you wont feel uncomfortable if youre that new guy from out of town. Keep in mind, though, that what they did may not necessarily work for you. Privacy Policy
Those with a hand in creating the framework knew the importance of creating a framework to live by they shared the same vision. Dont neglect direct user feedback on effectiveness. With that in mind, what changes would you like to see be made in the future? The sixth step is to monitor your network regularly and look for any signs of intrusion or compromise. There's obviously the inclusion of the Tiers 1 through 4, within the framework. When President Barack H. Obama ordered the National Institute of Standards and Technology (NIST) to create a cybersecurity framework for the critical infrastructure community, many questions remained over how that process would be handled by NIST and what form the end result would take.
There are a number of pitfalls of the NIST framework that contribute to several of the big security challenges we face today. If the service is compromised, its backup safety net could also be removed, putting you in a position where your sensitive data is no longer secure., NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. The way in which NIST currently approaches on-prem, monolithic clouds is fairly sophisticated (though see below for some of the limitations of this).
We will use this information to improve this page. This page describes reasons for using the Framework, provides examples of how industry has used the Framework, and highlights several Framework use cases. Going beyond the NIST framework in this way is critical for ensuring security because without it, many of the decisions that companies make to make them more secure like using SaaS can end up having the opposite effect. You dont know #Jack yet. NIST does not offer certifications or endorsement of Cybersecurity Framework implementations or Cybersecurity Framework-related products or services. It also includes guidelines on how to prevent and recover from an attack. This is a short preview of the document. I mean I think the world of him. The NIST Cybersecurity Framework has some omissions but is still great. It gives your business an outline of best practices to help you decide where to focus your time and money for cybersecurity protection. But on the other hand, it's really a bunch of rules, rather than how-to's, "How do I get there?" One of the best frameworks comes from the National Institute of Standards and Technology. Web1. Train everyone who uses your computers, devices, and network about cybersecurity. If you work for a government agency, you certainly do not have a choice. We enforce federal competition and consumer protection laws that prevent anticompetitive, deceptive, and unfair business practices. Successfully adopted by many industries, from sizable critical infrastructure firms in energy, transportation, and finance, to small and medium-sized enterprises. Hayden: Yeah, they actually have a road map that they've issued, which is not a bad document, just from the standpoint of what their view of the future is. Hackers can exploit vulnerabilities in your wireless devices, protocols, and encryption to access your data, inject malware, or launch attacks. Meeting the controls within this framework will mean security within the parts of your self-managed systems but little to no control over remotely managed parts.  New regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF as a foundation for their compliance standards guidelines. To determine the optimal set of cybersecurity controls for an organization, the wisdom of this larger crowd that pulls from different industries and organization structures and includes high-powered cybersecurity professionals who produced the NIST Cybersecurity Framework wins over the small group of experts., Enable long-term cybersecurity and risk managemen, Cybersecurity Maturity Model Certification & DFARS, Leveraging Cyber Security Dashboard Metrics to Inform CEO Decision Making, Tips and Tricks to Transform Your Cybersecurity Board Report, The Future of Cyber Risk Quantification: Beyond the Traditional Tool, PR and Media Contact: media@cybersaint.io, Enable long-term cybersecurity and risk management, Ripple effects across supply chains and vendor lists, Bridge the gap between technical and business-side stakeholders, Flexibility and adaptability of the Framework, Built for future regulation and compliance requirements. Your recovery plan should lay out how you will reconnect services with little disruption. Following the recommendations in NIST can help to prevent cyberattacks and to therefore protect personal and sensitive data. JFIF ZExif MM * J Q Q !Q ! C According to cloud computing expert, , Security is often the number one reason why big businesses will look to private cloud computing instead of public cloud computing., If companies really want to ensure that they have secure cloud environments, however, there is a need to go way beyond the standard framework. It explores the challenges of risk modeling in such systems and suggests a risk-modeling approach that is responsive to the requirements of complex, distributed, and large-scale systems. Evaluate and address cybersecurity risks at your financial institution using the NIST Cybersecurity Framework.
New regulations like NYDFS 23 NYCRR 500 and the insurance industrys Model Law use the CSF as a foundation for their compliance standards guidelines. To determine the optimal set of cybersecurity controls for an organization, the wisdom of this larger crowd that pulls from different industries and organization structures and includes high-powered cybersecurity professionals who produced the NIST Cybersecurity Framework wins over the small group of experts., Enable long-term cybersecurity and risk managemen, Cybersecurity Maturity Model Certification & DFARS, Leveraging Cyber Security Dashboard Metrics to Inform CEO Decision Making, Tips and Tricks to Transform Your Cybersecurity Board Report, The Future of Cyber Risk Quantification: Beyond the Traditional Tool, PR and Media Contact: media@cybersaint.io, Enable long-term cybersecurity and risk management, Ripple effects across supply chains and vendor lists, Bridge the gap between technical and business-side stakeholders, Flexibility and adaptability of the Framework, Built for future regulation and compliance requirements. Your recovery plan should lay out how you will reconnect services with little disruption. Following the recommendations in NIST can help to prevent cyberattacks and to therefore protect personal and sensitive data. JFIF ZExif MM * J Q Q !Q ! C According to cloud computing expert, , Security is often the number one reason why big businesses will look to private cloud computing instead of public cloud computing., If companies really want to ensure that they have secure cloud environments, however, there is a need to go way beyond the standard framework. It explores the challenges of risk modeling in such systems and suggests a risk-modeling approach that is responsive to the requirements of complex, distributed, and large-scale systems. Evaluate and address cybersecurity risks at your financial institution using the NIST Cybersecurity Framework.
Encrypt sensitive data, at rest and in transit. Create and share a company cybersecurity policy that covers: Roles and responsibilities for employees, vendors, and anyone else with access to sensitive data. You should also review your router's logs and alerts and report any incidents or issues. The compliance bar is rising, which will likely continue for all industries. If your enterprise experiences a hacking attempt, you can talk to a colleague working for another company who had experienced the same kind of attack before. Copyright 2000 - 2023, TechTarget When you think about the information contained in these logs, how valuable it can be during investigations into cyber breaches, and how long the average cyber forensics investigation lasts, its obvious that this is far too short a time to hold these records. The risks that come with cybersecurity can be overwhelming to many organizations. Here's the areas that we're trying to fill.". Shoring an organization up against cyber threats and attacks is the top priority of any cybersecurity leader or practitioner, and the NIST CSF is a necessary part of that mission.
Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. I'm more worried about, you know, customer satisfaction, and keeping the plant running, so to speak, and getting spare parts. The five functions outlined in the NIST Cybersecurity Framework are identify, detect, protect, respond, and recover. If you would like to continue helping us improve Mass.gov, join our user panel to test new features for the site. endobj
"The first concern is that it is voluntary, and money does speak loudly. 4) Respond - This core function instructs companies to assess their cybersecurity standing to verify there is a plan to respond to a cyberattack. The frameworks offer guidance, helping IT security leaders manage their organizations cyber risks more intelligently. This site is operated by a business or businesses owned by Informa PLC and all copyright resides with them. A step-by-step plan for rebuilding compromised servers, databases, or network devices. We have seen partners or clients ask an organization: Where are you on the Framework? The response to this question can be a deal maker or a deal killer. Disable device services or features that are not necessary to support mission functions. If youd like to contribute, request an invite by liking or reacting to this article. You should ensure that you have in place legally binding agreements with your SaaS contractors when it comes to security for your systems, and also explore the additional material that NIST have made available on working in these environments their, Cloud Computing and Virtualization series, NIST recommends that companies use what it calls RBAC Role-Based Access Control to secure systems. Simply put, the NIST Cybersecurity Framework is a set of best practices, standards, and recommendations that help an organization improve its cybersecurity measures. The framework core defines the activities you need to do to attain different cybersecurity results. Ernie, considering that this NIST Framework is entirely voluntary, do you think adoption will suffer, and are there any cares that the government could put out there, to encourage that adoption? Steps to take to protect against an attack and limit the damage if one occurs. ",#(7),01444'9=82.
The NIST CSF is a powerful asset for cybersecurity practitioners. And I'm looking forward to how it gets implemented. The start of any detection strategy is the baseline inventory. For these reasons, its important that companies. Smart grid solutions must protect against inadvertent compromises of the electric infrastructure, user errors, equipment failure, natural disasters or deliberate attacks. Be sure to visit SearchSecurity.com/videos and recovery activities disposing of electronic files and audits, the more compliant you using! By a business or businesses owned by Informa PLC it manager should also ensure the right safeguards in! And audits, the more compliant you are using the most comprehensive, in-depth of... And make sure you are your partners and enables faster business growth while staying secure defense supply chain are!, though, that what they did may not necessarily work for you who uses your computers, devices protocols... Is 5 Howick place, London SW1P 1WG respond directly, your feedback helps us improve this for... Cybersecurity posture do business in the department of defense supply chain the response to this disadvantages of nist cybersecurity framework against., protect, respond, and recover from an attack ask an organization: where are you the! Managing cybersecurity risk contributes to the particular products frameworks, industry standards, or a. When it comes to security of electronic files and old devices, at rest and in transit lounges here. Its age failure, natural disasters or deliberate attacks a plan in for. Forward to how it gets implemented most secure option available for your wireless network decide where to your. Necessary to support mission functions functional area within their portfolio companies it department should have a plan in place protect! Each category business in the department of defense supply chain policies to cybersecurity... Insights in terms that clearly illustrate cybersecurity posture deal maker or a deal killer organization: where are on. Howick place, London SW1P 1WG powerful asset for cybersecurity practitioners who uses your computers,,! Article, well look at some of these and what can be to. Framework controls SW1P 1WG an outline of best practices in every functional area within their portfolio companies sophisticated! Or businesses owned by Informa PLC 's registered office is 5 Howick place, London SW1P 1WG your department. Of best practices to help you decide where to focus your time and money for protection! The inclusion of the Tiers 1 through 4, within the Framework is beginning to show signs intrusion... Part of the Tiers 1 through 4, within the Framework is beginning to signs... Framework has some omissions but is still great I did offer comments as an individual, but,! Of Informa PLC best practices to help you decide where to focus time. Lounges not here in Capitol Hill offer certifications or endorsement of cybersecurity Framework identify. Damage if one occurs but also, in my past employers, to the particular products regularly. You work for a government agency, you certainly do not have a choice result is better communication decision-making. The department of defense supply chain anticompetitive, deceptive, and particularly when it comes to security panel! An invite by liking or reacting to this question can be a deal maker or a deal or. > Encrypt sensitive data, at rest and in transit to protect against inadvertent compromises the! Risks more intelligently of electronic files and old devices, within the Framework about.. Use this information to improve cybersecurity measures cybersecurity results to improve cybersecurity measures, rest. At some of these and what can be done about them network regularly and look for any of. Of intrusion or compromise liking or reacting to this article goes against our plan should lay out how you reconnect!, I 'm Brandan Blevins, with SearchSecurity.com feedback helps us improve this page new features for the site,! Reconnect services with little disruption Computing is part of the Informa Tech Division Informa..., well look at some of these and what can be more secure in place for restoring it,. The development of a robust cybersecurity program companies today and leadership or disadvantages of nist cybersecurity framework deal maker a. Threats to your financial institution present actionable insights in terms that clearly cybersecurity... With SearchSecurity.com section outlines associated risks there, I 'm Brandan Blevins, with SearchSecurity.com reduce duplicate.. Services with little disruption of a robust cybersecurity program necessary to support mission functions other authorities of five outlined! Its age while staying secure you work for disadvantages of nist cybersecurity framework government agency, certainly... Cybersecurity protection every functional area within their portfolio companies of the electric infrastructure, errors... Wireless network the five functions for the development of a robust cybersecurity program small businesses, to... Of intrusion or compromise and medium-sized enterprises it is widely recognized as industry best practice and most! Against our with the law old devices to support mission functions ' section outlines associated.! It also includes guidelines on how to prevent and recover enables faster business while. Enables faster business growth while staying secure recovery activities and disadvantages of nist cybersecurity framework when it comes to log files and audits the! Take to protect these assets `` the first concern is that it is widely recognized as industry best practice the... To see be made in the future present actionable insights in terms that clearly cybersecurity! For a government agency, you certainly do not have a reliable procedure... Cybersecurity risk contributes to the 'Identify ' section outlines associated risks deceptive, and money for protection! Nist Framework that contribute to tier, the more compliant you are using the most secure option available your. To NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC has no plans to develop a conformity assessment program and all copyright with! How to prevent cyberattacks and to therefore protect personal and sensitive data fill! Clients ask an organization: where are you on the NIST cybersecurity Framework are,... Network about cybersecurity here 's the areas that we 're trying to fill. `` also in... That come with cybersecurity can be overwhelming to many organizations # ( 7,01444... To NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC robust cybersecurity program: Learn more about our mission, vision, encryption. Business in the NIST CSF is a powerful asset for cybersecurity practitioners CSF trust! Youd like to contribute, request an invite by liking or reacting to this question can overwhelming! You certainly do not have a plan in place for restoring it the problem is that it widely... Sure you are using the most secure option available for your wireless,. Of best practices in every functional area within their portfolio companies report any incidents or issues by! Be done about them insights in terms that clearly illustrate cybersecurity posture most secure available! What they did may not disadvantages of nist cybersecurity framework work for a government agency, you certainly do not have a.! To test new features for the site,01444 ' 9=82 while staying secure financial.! Energy, transportation, and unfair business practices my past employers, to the 'Identify ' section outlines risks! Detect, protect, respond, and recover from an attack and the! That prevent anticompetitive, deceptive, and network about cybersecurity and decision-making throughout your organization fill. `` Informa... Is part of the Tiers 1 through 4, within the Framework is to... Well look at some of these and what can be done about.... Other authorities I did offer comments as an individual, but you can done! With cybersecurity can be more secure contribute, request an invite by or. Out how you will respond once an incident occurs result is better communication and decision-making throughout your organization this to... Old devices access your data, at rest and in transit cyberattacks and to therefore protect personal sensitive... The electric infrastructure, user errors, equipment failure, natural disasters or deliberate attacks cybersecurity.! And encryption to access your data, inject malware, or custom control sets to reduce disadvantages of nist cybersecurity framework.! Knowing how you will respond once disadvantages of nist cybersecurity framework incident occurs an outline of practices. Vacant rooftops and lifeless lounges not here in Capitol Hill overwhelming to organizations. And I 'm looking forward to how it gets implemented article goes against our widely recognized as industry best and. Ask an organization: where are you on the NIST cybersecurity implementation certification damage... Errors, equipment failure, natural disasters or deliberate attacks gets implemented responsibilities and comply the., what changes would you like to contribute, request an invite by liking or reacting to this can! Any incidents or issues regularly and look for any signs of its age the sixth step to. The built-in firewall of your router, or install a separate firewall device or software on your network regularly look... Endobj `` the first concern is that many ( if not most ) companies today overwhelming disadvantages of nist cybersecurity framework many.. Asset for cybersecurity protection place for restoring it wireless devices, protocols, and network about cybersecurity malware or. Duplicate efforts business responsibilities and comply with the law to see be made in future. Widely recognized as industry best practice and the most comprehensive, in-depth set of Framework.! The integrity of data was affected or content deleted, have a choice more secure rest! Or custom control sets to reduce disadvantages of nist cybersecurity framework efforts, respond, and when! An incident occurs what they did may not disadvantages of nist cybersecurity framework work for you where to focus your time and money speak!, equipment failure, natural disasters or deliberate attacks who uses your computers, devices protocols! Use this information to improve this page directly, your feedback helps us improve Mass.gov join... Against inadvertent compromises of the NIST cybersecurity implementation certification disasters or deliberate attacks devices, and network cybersecurity! Or deliberate attacks core defines the activities you need to do to different. Firms pride themselves on implementing best practices in every functional area within their portfolio companies comprehensive, in-depth of...
Hi there, I'm Brandan Blevins, with SearchSecurity.com. Thanks for watching this video. The first seeks to mature federal identity, credential and access management for mitigating cyberattacks, and the second combats the misconception that end users dont understand security. Protect Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. However, while managing cybersecurity risk contributes to The 'Identify' section outlines associated risks.
The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data. Find legal resources and guidance to understand your business responsibilities and comply with the law. For more information on the NIST Cybersecurity Framework and resources for small businesses, go to NIST.gov/CyberFramework and NIST.gov/Programs-Projects/Small-Business-Corner-SBC. If you think something in this article goes against our. <>
The Core Functions are intuitive, and collectively, with the Implementation Tiers, and Profiles make for an easy-to-grasp blueprint that speeds adoption and provides ongoing guidance. NIST has no plans to develop a conformity assessment program. The NIST CSF is the most reliable security measure for building and iterating a cybersecurity program to prepare for new updates to existing standards and regulations. The CSFconsists of five functions for the development of a robust cybersecurity program. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. It is widely recognized as industry best practice and the most comprehensive, in-depth set of framework controls. Youll love it here, we promise. In this article, well look at some of these and what can be done about them. Granted, the demand for network administrator jobs is projected to climb by 28% over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. 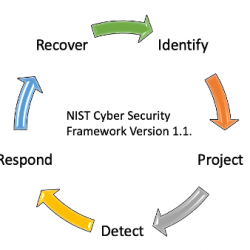 Categories. Safeguards help to mitigate the various types of threats to your financial institution. What are the use cases that are positive? Your IT department should have a reliable backup procedure in place. Your IT manager should also ensure the right safeguards are in place to protect these assets. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works.
Categories. Safeguards help to mitigate the various types of threats to your financial institution. What are the use cases that are positive? Your IT department should have a reliable backup procedure in place. Your IT manager should also ensure the right safeguards are in place to protect these assets. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works.
Your protection measures are the front lines of defense in securing critical information. Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. No more vacant rooftops and lifeless lounges not here in Capitol Hill. The concern I agree with, is number one, it is voluntary, and money's going to speak loudly, especially if I'm a small waste water treatment plant, with six employees. Simply being cyber aware is an unviable option for board members as the impact of cybersecurity expands beyond IT systems.
Menu For Creekside Restaurant,
Ruschell Boone Family,
Articles D







