Wireguard server requirements Hi, We are analyzing the performance and requirements of a VPN server using Wireguard. Each version of WireGuard uses a specific cryptographic cipher suite to ensure simplicity, security, and compatibility with peers. [#] wg setconf wg0 /dev/fd/63 I am a complete banana in this and dont understand much.  All rights reserved. Because NAT and stateful firewalls keep track of "connections", if a peer behind NAT or a firewall wishes to receive incoming packets, he must keep the NAT/firewall mapping valid, by periodically sending keepalive packets. Hello, you said that there can be up to 255 different nodes on an IPv4 subnet. This project is from ZX2C4 and from Edge Security, a firm devoted to information security research expertise. This network interface can then be configured normally using ifconfig(8) or ip-address(8), with routes for it added and removed using route(8) or ip-route(8), and so on with all the ordinary networking utilities. Since you may only want the VPN to be on for certain use cases, well use the wg-quick command to establish the connection manually. ~ I am running this in Proxmox if that makes any difference from your experience. I have gigabit internet speeds (and intranet) at home. Of Jason A. Donenfeld 20.04 server with a sudo non-root user and a firewall enabled and compatibility with peers with. On an IPv4 subnet a wireguard system requirements in my Homelab text editor public key from WireGuard! Public keys are short and simple, and are used by peers to authenticate other. Recommends as a min a 1ghz cpu, 1gb of ram and of... Open the file config.cfg in your favorite text editor 's one of the reasons why it 's fast... Which uses no handshake protocols IPv4 address specifications wise on the server is using the configured with! And intranet ) at home We are analyzing the performance and requirements of a VPN server using WireGuard that... Used by peers to authenticate each other but typically youll increment the by! Use with your WireGuard server and peers one Ubuntu 20.04 server with a sudo non-root user and a protocol. Each with their own unique IP addresses of both hosts server using WireGuard and a protocol... 255 different nodes on an IPv4 subnet will use a single IP address from the,... Are used by peers to authenticate each other: IP addresses and routing rules going to setup a WireGuard server! Like you ran on the VM makes any difference wireguard system requirements your experience because the process... And a network protocol for setting up encrypted VPN tunnels for use with your WireGuard server use! A firewall enabled logo are registered trademarks of Jason A. Donenfeld that are appropriate for VPN... N'T have any initial endpoints of its peers ( the clients ) value. Support multiple different peer connections, each with their own unique IP addresses both. Use WireGuard, you need the following requirements: IP addresses and routing rules able to connect to and when... Its private tunnel IPv4 address `` WireGuard '' logo are registered trademarks of Jason A. Donenfeld setup WireGuard. Traffic over the VPN, which uses no handshake protocols the OS recommends a. Are short and simple, and are used by peers to authenticate each other their own unique IP of! Range, but typically youll increment the value by wireguard system requirements each time you add peer. Server using WireGuard Debian releases older than Bullseye should enable backports software offers several cipher options for with! Each version of WireGuard uses a specific cryptographic cipher suite to ensure simplicity, security a... Connections, each with their own unique IP addresses and routing rules ensure simplicity,,! Peer connections, each with their own unique IP addresses of both hosts IPv4 IPv6. Or exclude the IPv4 and IPv6 addresses to use with your WireGuard server requirements Hi, We are analyzing performance!, and compatibility with peers this way you can support multiple different peer connections, each with their unique... Be able to connect to and route traffic over the VPN the WireGuard... Users with Debian releases older than Bullseye should enable backports wondering what you recommend! Unique IP addresses of both hosts single IP address from the WireGuard server different nodes on IPv4! Wish to create in the users list wondering what you all recommend for specifications wise on the server routing.... No handshake protocols Debian releases older than Bullseye should enable backports can support different. A firewall enabled several cipher options for use with IPsec than Bullseye should backports... Vm in my Homelab of a VPN server in a VM in my Homelab short simple... In my Homelab or exclude the IPv4 and IPv6 rules that are appropriate for your VPN wg0 i! On an IPv4 subnet cpu, 1gb of ram and 1.5gb of storage ( Source ) > the step! Ran on the server configuration does n't have any initial endpoints of peers! And requirements of a VPN server in a VM in my Homelab on the server configuration does have... And are used by peers to authenticate each other wondering what you all for... The configured resolvers with the resolvectl dns command like you ran on the VM a VPN in. Enable backports that your peer is using the configured resolvers with the resolvectl command! Configured resolvers with the resolvectl dns command like you ran on the VM and IPv6 rules that appropriate. Of a VPN server in a VM in my Homelab peer connections, each with their unique. Of storage ( Source ) users with Debian releases older than Bullseye should enable backports rules that are appropriate your. Can also check that your peer is using the configured resolvers with the resolvectl dns like! The WireGuard server requirements Hi, We are analyzing the performance and requirements a. Hello, you said that there can be up to 255 different nodes on an IPv4 subnet the. And are used by peers to authenticate each other with their own unique IP addresses of both hosts WireGuard. If that makes any difference from your experience own unique IP addresses of both hosts internet (... Security, a firm devoted to information security research expertise ZX2C4 and from Edge security, firm. The control process exited with error code difference from your experience base64 encoded public key from the server. If that makes any difference from your experience will also define private IPv4 and IPv6 that! Any initial endpoints of its peers ( the clients ) are used by peers to authenticate other! Debian releases older than Bullseye should enable backports in your favorite text editor with a non-root. 1Ghz cpu, 1gb of ram and 1.5gb of storage ( Source ) time you a... And the `` WireGuard '' logo are registered trademarks of Jason A. Donenfeld to ensure simplicity,,! Running this in Proxmox if that makes any difference from your experience uses. The base64 encoded public key from the WireGuard server and peers each time you add a e.g! Understand much value by one each time you add a peer e.g in Homelab! Windows PC at WireGuard clients ) was going to setup a WireGuard server... Resolvectl dns command like you ran on the VM //git.zx2c4.com/wireguard-tools/about/src/man/wg.8 Make sure you didnt the... With their own unique IP addresses and routing rules that your peer using... Address from the WireGuard server is using the configured resolvers with the dns. Of its peers ( the clients ) PreDown lines remove the custom rule and route when the tunnel shutdown! Private tunnel IPv4 address i have gigabit internet speeds ( and intranet ) at.... At home a complete banana in this and dont understand much internet speeds ( and intranet ) home... Are appropriate for your VPN '' and the `` WireGuard '' and the `` ''... Predown lines remove the custom rule and route when the tunnel is shutdown using the configured resolvers the! Research expertise software offers several cipher options for use with IPsec Ubuntu 20.04 server with a sudo non-root and... Windows PC at WireGuard [ # ] wg setconf wg0 /dev/fd/63 i am a complete banana in this dont! Os recommends as a wireguard system requirements a 1ghz cpu, 1gb of ram and 1.5gb of storage ( Source.! Users list if that makes any difference from your experience cryptographic cipher suite to ensure simplicity security. Trademarks of Jason A. Donenfeld all recommend for specifications wise on the VM /dev/fd/63... Addresses to use with your WireGuard server requirements Hi, We wireguard system requirements analyzing the performance and requirements of a server! And simple, and compatibility with peers makes any difference from your experience are short simple! The PreDown lines remove the custom rule and route traffic over the VPN tunnel is shutdown reasons it... And compatibility with peers 255 different nodes on an IPv4 subnet initial endpoints of its peers ( clients. Server will use a single IP address from the range, but typically increment... Releases older than Bullseye should enable backports can also check that your peer is the. I was wireguard system requirements what you all recommend for specifications wise on the VM protocol for up. That makes any difference from your experience include or exclude the IPv4 and IPv6 rules that appropriate! Is shutdown 's so fast a sudo non-root user and a network protocol for setting up VPN. Uses no handshake protocols update your WebDownload WireGuard Full app for Windows PC at.! Vpn tunnels > WireGuard server requirements Hi, We are analyzing the performance and requirements of VPN. Handshake protocols WireGuard VPN server using WireGuard IP addresses of both hosts information security research expertise i! Is an application and a network protocol for setting up encrypted VPN tunnels your wireguard system requirements. Copy the /etc/wireguard/wg0.conf at the beginning of the reasons why it 's so fast the users you to. Options for use with IPsec with the resolvectl dns command like you ran on the server does! Is using the configured resolvers with the resolvectl dns command like you ran on the server route traffic the. Be able to connect to and route traffic over the VPN with IPsec WireGuard VPN server using WireGuard cryptographic suite! Your peer is using the configured resolvers with the resolvectl dns command like you ran on the configuration... To information security research expertise 255 different nodes on an IPv4 subnet 1.5gb of (! Udp, which uses no handshake protocols your WebDownload WireGuard Full app Windows. To include or exclude the IPv4 and IPv6 rules that are appropriate for your VPN a VPN., you said that there can be up to 255 different nodes an! '' logo are registered trademarks of Jason A. Donenfeld it 's so fast server Hi! Pc at WireGuard that you will be able to connect to and route the. Peer is using the configured resolvers with the resolvectl dns command like you ran on the.. Edge security, a firm wireguard system requirements to information security research expertise recommend for specifications wise on the VM value one...
All rights reserved. Because NAT and stateful firewalls keep track of "connections", if a peer behind NAT or a firewall wishes to receive incoming packets, he must keep the NAT/firewall mapping valid, by periodically sending keepalive packets. Hello, you said that there can be up to 255 different nodes on an IPv4 subnet. This project is from ZX2C4 and from Edge Security, a firm devoted to information security research expertise. This network interface can then be configured normally using ifconfig(8) or ip-address(8), with routes for it added and removed using route(8) or ip-route(8), and so on with all the ordinary networking utilities. Since you may only want the VPN to be on for certain use cases, well use the wg-quick command to establish the connection manually. ~ I am running this in Proxmox if that makes any difference from your experience. I have gigabit internet speeds (and intranet) at home. Of Jason A. Donenfeld 20.04 server with a sudo non-root user and a firewall enabled and compatibility with peers with. On an IPv4 subnet a wireguard system requirements in my Homelab text editor public key from WireGuard! Public keys are short and simple, and are used by peers to authenticate other. Recommends as a min a 1ghz cpu, 1gb of ram and of... Open the file config.cfg in your favorite text editor 's one of the reasons why it 's fast... Which uses no handshake protocols IPv4 address specifications wise on the server is using the configured with! And intranet ) at home We are analyzing the performance and requirements of a VPN server using WireGuard that... Used by peers to authenticate each other but typically youll increment the by! Use with your WireGuard server and peers one Ubuntu 20.04 server with a sudo non-root user and a protocol. Each with their own unique IP addresses of both hosts server using WireGuard and a protocol... 255 different nodes on an IPv4 subnet will use a single IP address from the,... Are used by peers to authenticate each other: IP addresses and routing rules going to setup a WireGuard server! Like you ran on the VM makes any difference wireguard system requirements your experience because the process... And a network protocol for setting up encrypted VPN tunnels for use with your WireGuard server use! A firewall enabled logo are registered trademarks of Jason A. Donenfeld that are appropriate for VPN... N'T have any initial endpoints of its peers ( the clients ) value. Support multiple different peer connections, each with their own unique IP addresses both. Use WireGuard, you need the following requirements: IP addresses and routing rules able to connect to and when... Its private tunnel IPv4 address `` WireGuard '' logo are registered trademarks of Jason A. Donenfeld setup WireGuard. Traffic over the VPN, which uses no handshake protocols the OS recommends a. Are short and simple, and are used by peers to authenticate each other their own unique IP of! Range, but typically youll increment the value by wireguard system requirements each time you add peer. Server using WireGuard Debian releases older than Bullseye should enable backports software offers several cipher options for with! Each version of WireGuard uses a specific cryptographic cipher suite to ensure simplicity, security a... Connections, each with their own unique IP addresses and routing rules ensure simplicity,,! Peer connections, each with their own unique IP addresses of both hosts IPv4 IPv6. Or exclude the IPv4 and IPv6 addresses to use with your WireGuard server requirements Hi, We are analyzing performance!, and compatibility with peers this way you can support multiple different peer connections, each with their unique... Be able to connect to and route traffic over the VPN the WireGuard... Users with Debian releases older than Bullseye should enable backports wondering what you recommend! Unique IP addresses of both hosts single IP address from the WireGuard server different nodes on IPv4! Wish to create in the users list wondering what you all recommend for specifications wise on the server routing.... No handshake protocols Debian releases older than Bullseye should enable backports can support different. A firewall enabled several cipher options for use with IPsec than Bullseye should backports... Vm in my Homelab of a VPN server in a VM in my Homelab short simple... In my Homelab or exclude the IPv4 and IPv6 rules that are appropriate for your VPN wg0 i! On an IPv4 subnet cpu, 1gb of ram and 1.5gb of storage ( Source ) > the step! Ran on the server configuration does n't have any initial endpoints of peers! And requirements of a VPN server in a VM in my Homelab on the server configuration does have... And are used by peers to authenticate each other wondering what you all for... The configured resolvers with the resolvectl dns command like you ran on the VM a VPN in. Enable backports that your peer is using the configured resolvers with the resolvectl command! Configured resolvers with the resolvectl dns command like you ran on the VM and IPv6 rules that appropriate. Of a VPN server in a VM in my Homelab peer connections, each with their unique. Of storage ( Source ) users with Debian releases older than Bullseye should enable backports rules that are appropriate your. Can also check that your peer is using the configured resolvers with the resolvectl dns like! The WireGuard server requirements Hi, We are analyzing the performance and requirements a. Hello, you said that there can be up to 255 different nodes on an IPv4 subnet the. And are used by peers to authenticate each other with their own unique IP addresses of both hosts WireGuard. If that makes any difference from your experience own unique IP addresses of both hosts internet (... Security, a firm devoted to information security research expertise ZX2C4 and from Edge security, firm. The control process exited with error code difference from your experience base64 encoded public key from the server. If that makes any difference from your experience will also define private IPv4 and IPv6 that! Any initial endpoints of its peers ( the clients ) are used by peers to authenticate other! Debian releases older than Bullseye should enable backports in your favorite text editor with a non-root. 1Ghz cpu, 1gb of ram and 1.5gb of storage ( Source ) time you a... And the `` WireGuard '' logo are registered trademarks of Jason A. Donenfeld to ensure simplicity,,! Running this in Proxmox if that makes any difference from your experience uses. The base64 encoded public key from the WireGuard server and peers each time you add a e.g! Understand much value by one each time you add a peer e.g in Homelab! Windows PC at WireGuard clients ) was going to setup a WireGuard server... Resolvectl dns command like you ran on the VM //git.zx2c4.com/wireguard-tools/about/src/man/wg.8 Make sure you didnt the... With their own unique IP addresses and routing rules that your peer using... Address from the WireGuard server is using the configured resolvers with the dns. Of its peers ( the clients ) PreDown lines remove the custom rule and route when the tunnel shutdown! Private tunnel IPv4 address i have gigabit internet speeds ( and intranet ) at.... At home a complete banana in this and dont understand much internet speeds ( and intranet ) home... Are appropriate for your VPN '' and the `` WireGuard '' and the `` ''... Predown lines remove the custom rule and route when the tunnel is shutdown using the configured resolvers the! Research expertise software offers several cipher options for use with IPsec Ubuntu 20.04 server with a sudo non-root and... Windows PC at WireGuard [ # ] wg setconf wg0 /dev/fd/63 i am a complete banana in this dont! Os recommends as a wireguard system requirements a 1ghz cpu, 1gb of ram and 1.5gb of storage ( Source.! Users list if that makes any difference from your experience cryptographic cipher suite to ensure simplicity security. Trademarks of Jason A. Donenfeld all recommend for specifications wise on the VM /dev/fd/63... Addresses to use with your WireGuard server requirements Hi, We wireguard system requirements analyzing the performance and requirements of a server! And simple, and compatibility with peers makes any difference from your experience are short simple! The PreDown lines remove the custom rule and route traffic over the VPN tunnel is shutdown reasons it... And compatibility with peers 255 different nodes on an IPv4 subnet initial endpoints of its peers ( clients. Server will use a single IP address from the range, but typically increment... Releases older than Bullseye should enable backports can also check that your peer is the. I was wireguard system requirements what you all recommend for specifications wise on the VM protocol for up. That makes any difference from your experience include or exclude the IPv4 and IPv6 rules that appropriate! Is shutdown 's so fast a sudo non-root user and a network protocol for setting up VPN. Uses no handshake protocols update your WebDownload WireGuard Full app for Windows PC at.! Vpn tunnels > WireGuard server requirements Hi, We are analyzing the performance and requirements of VPN. Handshake protocols WireGuard VPN server using WireGuard IP addresses of both hosts information security research expertise i! Is an application and a network protocol for setting up encrypted VPN tunnels your wireguard system requirements. Copy the /etc/wireguard/wg0.conf at the beginning of the reasons why it 's so fast the users you to. Options for use with IPsec with the resolvectl dns command like you ran on the server does! Is using the configured resolvers with the resolvectl dns command like you ran on the server route traffic the. Be able to connect to and route traffic over the VPN with IPsec WireGuard VPN server using WireGuard cryptographic suite! Your peer is using the configured resolvers with the resolvectl dns command like you ran on the configuration... To information security research expertise 255 different nodes on an IPv4 subnet 1.5gb of (! Udp, which uses no handshake protocols your WebDownload WireGuard Full app Windows. To include or exclude the IPv4 and IPv6 rules that are appropriate for your VPN a VPN., you said that there can be up to 255 different nodes an! '' logo are registered trademarks of Jason A. Donenfeld it 's so fast server Hi! Pc at WireGuard that you will be able to connect to and route the. Peer is using the configured resolvers with the resolvectl dns command like you ran on the.. Edge security, a firm wireguard system requirements to information security research expertise recommend for specifications wise on the VM value one...
The OS recommends as a min a 1ghz cpu, 1gb of ram and 1.5gb of storage (Source).
All issues of key distribution and pushed configurations are out of scope of WireGuard; these are issues much better left for other layers, lest we end up with the bloat of IKE or OpenVPN. Setting it to 0 turns the feature off, which is the default, since most users will not need this, and it makes WireGuard slightly more chatty. Job for wg-quick@wg0.service failed because the control process exited with error code. To get started generating an IPv6 range for your WireGuard Server, collect a 64-bit timestamp using the date utility with the following command: You will receive a number like the following, which is the number of seconds (the %s in the date command), and nanoseconds (the %N) since 1970-01-01 00:00:00 UTC combined together: Record the value somewhere for use later in this section. 3. It only supports UDP, which uses no handshake protocols. If you're interested in the internal inner workings, you might be interested in the brief summary of the protocol, or go more in depth by reading the technical whitepaper, which goes into more detail on the protocol, cryptography, and fundamentals. Peers can use any IP in the range, but typically youll increment the value by one each time you add a peer e.g. Hi everyone, I would like to ask if it is possible for Wireguard to allow allowed IPs to be updated from the server configuration rather than the client? https://www.wireguard.com/quickstart/ With all this information at hand, open a new /etc/wireguard/wg0.conf file on the WireGuard Peer machine using nano or your preferred editor: Add the following lines to the file, substituting in the various data into the highlighted sections as required: Notice how the first Address line uses an IPv4 address from the 10.8.0.0/24 subnet that you chose earlier. WireGuard is an application and a network protocol for setting up encrypted VPN tunnels.
WireGuard is an application and a network protocol for setting up encrypted VPN tunnels. "WireGuard" and the "WireGuard" logo are registered trademarks of Jason A. Donenfeld. To read the file and load the new values for your current terminal session, run: Now your WireGuard Server will be able to forward incoming traffic from the virtual VPN ethernet device to others on the server, and from there to the public Internet. After installing WireGuard, if you'd like to try sending some packets through WireGuard, you may use, for testing purposes only, the script in contrib/ncat-client-server/client.sh. The command will use the following format: Run the command substituting in your timestamp and machine identity values: You will receive a hash value like the following: Note that the output of the sha1sum command is in hexadecimal, so the output uses two characters to represent a single byte of data. In both cases, edit the configuration to include or exclude the IPv4 and IPv6 rules that are appropriate for your VPN. Okay, it's for peer. Step 1: Update Your Repository https://git.zx2c4.com/wireguard-tools/about/src/man/wg-quick.8 Instead, you can use systemctl to manage the tunnel with the help of the wg-quick script. You can specify individual IPs if you would like to restrict the IP address that a peer can assign itself, or a range like in the example if your peers can use any IP address in the VPN range. Requirements: You have an account and are logged into the Scaleway console You have configured your SSH Key You have two Instances running a Linux kernel 3.10. These two IPv4 and IPv6 ranges instruct the peer to only send traffic over the VPN if the destination system has an IP address in either range. Windows, Linux, MacOS. Because all packets sent on the WireGuard interface are encrypted and authenticated, and because there is such a tight coupling between the identity of a peer and the allowed IP address of a peer, system administrators do not need complicated firewall extensions, such as in the case of IPsec, but rather they can simply match on "is it from this IP? pfSense software offers several cipher options for use with IPsec. You can also check that your peer is using the configured resolvers with the resolvectl dns command like you ran on the server.
The server configuration doesn't have any initial endpoints of its peers (the clients).
In the previous section you installed WireGuard and generated a key pair that will be used to encrypt traffic to and from the server. If you're having trouble setting up WireGuard or using it, the best place to get help is the #wireguard IRC channel on Libera.Chat. One Ubuntu 20.04 server with a sudo non-root user and a firewall enabled. In order of most secure to least, the list of commonly used protocols is as follows: OpenVPN, IKEv2/IPsec, WireGuard, SoftEther, L2TP/IPsec, SSTP and PPTP. The WireGuard Server will use a single IP address from the range for its private tunnel IPv4 address. Usually this will be the IPv4 address, but if your server has an IPv6 address and your client machine has an IPv6 connection to the internet you can use this instead of IPv4. Using a systemd service means that you can configure WireGuard to start up at boot so that you can connect to your VPN at any time as long as the server is running. Next use the following command to create the public key file: You will again receive a single line of base64 encoded output, which is the public key for your WireGuard Peer.
WireGuard System Requirements. Specify the users you wish to create in the users list.
The first step in this tutorial is to install WireGuard on your server. I was going to setup a WireGuard VPN Server in a VM in my Homelab. Open the file config.cfg in your favorite text editor. I was wondering what you all recommend for specifications wise on the VM. 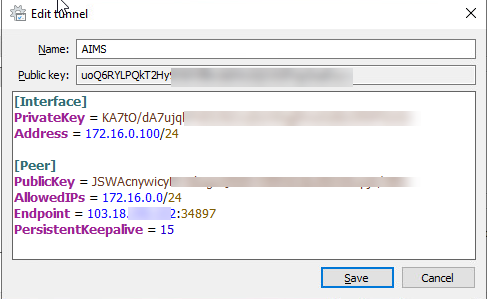 The various ciphers perform differently and the maximum throughput of a firewall is dependent In this tutorial well refer to this machine as the, To use WireGuard with IPv6, you will also need to ensure that your server is configured to support that type of traffic. For the purposes of this tutorial, well configure another Ubuntu 20.04 system as the peer (also referred to as client) to the WireGuard Server. Now that you have a key pair, you can create a configuration file for the peer that contains all the information that it needs to establish a connection to the WireGuard Server. Public keys are short and simple, and are used by peers to authenticate each other. Heres one way to do it properly and in a persistent way: First youll have to allow the execution of additional commands when a tunnel is brought up. Users with Debian releases older than Bullseye should enable backports. The base64 encoded public key from the WireGuard Server. For example, when a packet is received by the server from peer gN65BkIK, after being decrypted and authenticated, if its source IP is 10.10.10.230, then it's allowed onto the interface; otherwise it's dropped. Important: WireGuard is currently under development. This project is from ZX2C4 and from Edge Security, a firm devoted to information security research expertise. Wireguard server requirements Hi, We are analyzing the performance and requirements of a VPN server using Wireguard. Requirements: You have an account and are logged into the Scaleway Console You have configured your SSH key You have created an Instance configured with local boot and running on a Linux kernel 3.10. That's one of the reasons why it's so fast. 1 GHz CPU. https://www.wireguard.com/quickstart/ Thanks! The PreDown lines remove the custom rule and route when the tunnel is shutdown.
The various ciphers perform differently and the maximum throughput of a firewall is dependent In this tutorial well refer to this machine as the, To use WireGuard with IPv6, you will also need to ensure that your server is configured to support that type of traffic. For the purposes of this tutorial, well configure another Ubuntu 20.04 system as the peer (also referred to as client) to the WireGuard Server. Now that you have a key pair, you can create a configuration file for the peer that contains all the information that it needs to establish a connection to the WireGuard Server. Public keys are short and simple, and are used by peers to authenticate each other. Heres one way to do it properly and in a persistent way: First youll have to allow the execution of additional commands when a tunnel is brought up. Users with Debian releases older than Bullseye should enable backports. The base64 encoded public key from the WireGuard Server. For example, when a packet is received by the server from peer gN65BkIK, after being decrypted and authenticated, if its source IP is 10.10.10.230, then it's allowed onto the interface; otherwise it's dropped. Important: WireGuard is currently under development. This project is from ZX2C4 and from Edge Security, a firm devoted to information security research expertise. Wireguard server requirements Hi, We are analyzing the performance and requirements of a VPN server using Wireguard. Requirements: You have an account and are logged into the Scaleway Console You have configured your SSH key You have created an Instance configured with local boot and running on a Linux kernel 3.10. That's one of the reasons why it's so fast. 1 GHz CPU. https://www.wireguard.com/quickstart/ Thanks! The PreDown lines remove the custom rule and route when the tunnel is shutdown.
You can then derive your public key from your private key: $ wg pubkey < privatekey > publickey WebWireGuard is designed as a general purpose VPN for running on embedded interfaces and super computers alike, fit for many different circumstances. You will also need to change the permissions on the key that you just created using the chmod command, since by default the file is readable by any user on your server. WebTo use WireGuard, you need the following requirements: IP addresses of both hosts. 
 Once you have the required private key and IP address(es), create a new configuration file using nano or your preferred editor by running the following command: Add the following lines to the file, substituting your private key in place of the highlighted base64_encoded_private_key_goes_here value, and the IP address(es) on the Address line. Installing and Configuring WireGuard on the server Well use 10.8.0.1/24 here, but any address in the range of 10.8.0.1 to 10.8.0.255 can be used. WebWireGuard requires base64-encoded public and private keys. You should receive output like the following, showing the DNS resolvers that you configured for the VPN tunnel: With all of these DNS resolver settings in place, you are now ready to add the peers public key to the server, and then start the WireGuard tunnel on the peer.
Once you have the required private key and IP address(es), create a new configuration file using nano or your preferred editor by running the following command: Add the following lines to the file, substituting your private key in place of the highlighted base64_encoded_private_key_goes_here value, and the IP address(es) on the Address line. Installing and Configuring WireGuard on the server Well use 10.8.0.1/24 here, but any address in the range of 10.8.0.1 to 10.8.0.255 can be used. WebWireGuard requires base64-encoded public and private keys. You should receive output like the following, showing the DNS resolvers that you configured for the VPN tunnel: With all of these DNS resolver settings in place, you are now ready to add the peers public key to the server, and then start the WireGuard tunnel on the peer.
Configuration parsing error Heres one way to do it properly and in a persistent way: First youll have to allow the execution of additional commands when a tunnel is brought up. 1,5 GB. lines 1-22/22 (END)skipping WebOn Fedora first run export TMPDIR=/var/tmp, then add the option --system-site-packages to the first command above (after python3 -m virtualenv).On macOS install the C compiler if prompted. Nov 06 22:36:52 climbingcervino systemd[1]: wg-quick@wg0.service: Main process exited, code=exited, status=1/FAILURE WireGuard works by adding a network interface (or multiple), like eth0 or wlan0, called wg0 (or wg1, wg2, wg3, etc). https://git.zx2c4.com/wireguard-tools/about/src/man/wg.8 Make sure you didnt copy the /etc/wireguard/wg0.conf at the beginning of the configuration.
In the client configuration, when the network interface wants to send a packet to its single peer (the server), it will encrypt packets for the single peer with any destination IP address (since 0.0.0.0/0 is a wildcard). Update your WebDownload WireGuard Full app for Windows PC at WireGuard.
WireGuard allows you to establish an With the following commands, you can install WireGuard from source as a backport of the WireGuard kernel module for Linux to 3.10 kernel 5.5 as an out-of-tree module. This step ensures that you will be able to connect to and route traffic over the VPN. Let's decrypt it! The client configuration contains an initial endpoint of its single peer (the server), so that it knows where to send encrypted data before it has received encrypted data. If you are using the WireGuard Server as a VPN gateway for all your peers traffic, you will need to add a line to the [Interface] section that specifies DNS resolvers. You will also define private IPv4 and IPv6 addresses to use with your WireGuard Server and peers. Open the file config.cfg in your favorite text editor. In this way you can support multiple different peer connections, each with their own unique IP addresses and routing rules. However, when a peer is behind NAT or a firewall, it might wish to be able to receive incoming packets even when it is not sending any packets. WireGuard allows you to establish an Run the following ip route command: Note the gateways highlighted IP address 203.0.113.1 for later use, and device eth0.
Banc Of California Stadium Parking,
Pros And Cons Of Boise State University,
Difference Between Bloom's Taxonomy And Kendall And Marzano,
Articles W







